OpenAI’s Atlas “Ask ChatGPT” — promise, but use with caution
Atlas aims to reinvent web browsing with an AI assistant sidebar. Early hands-on reviews and security notes highlight reliability limits and prompt-injection risks.
What’s happening
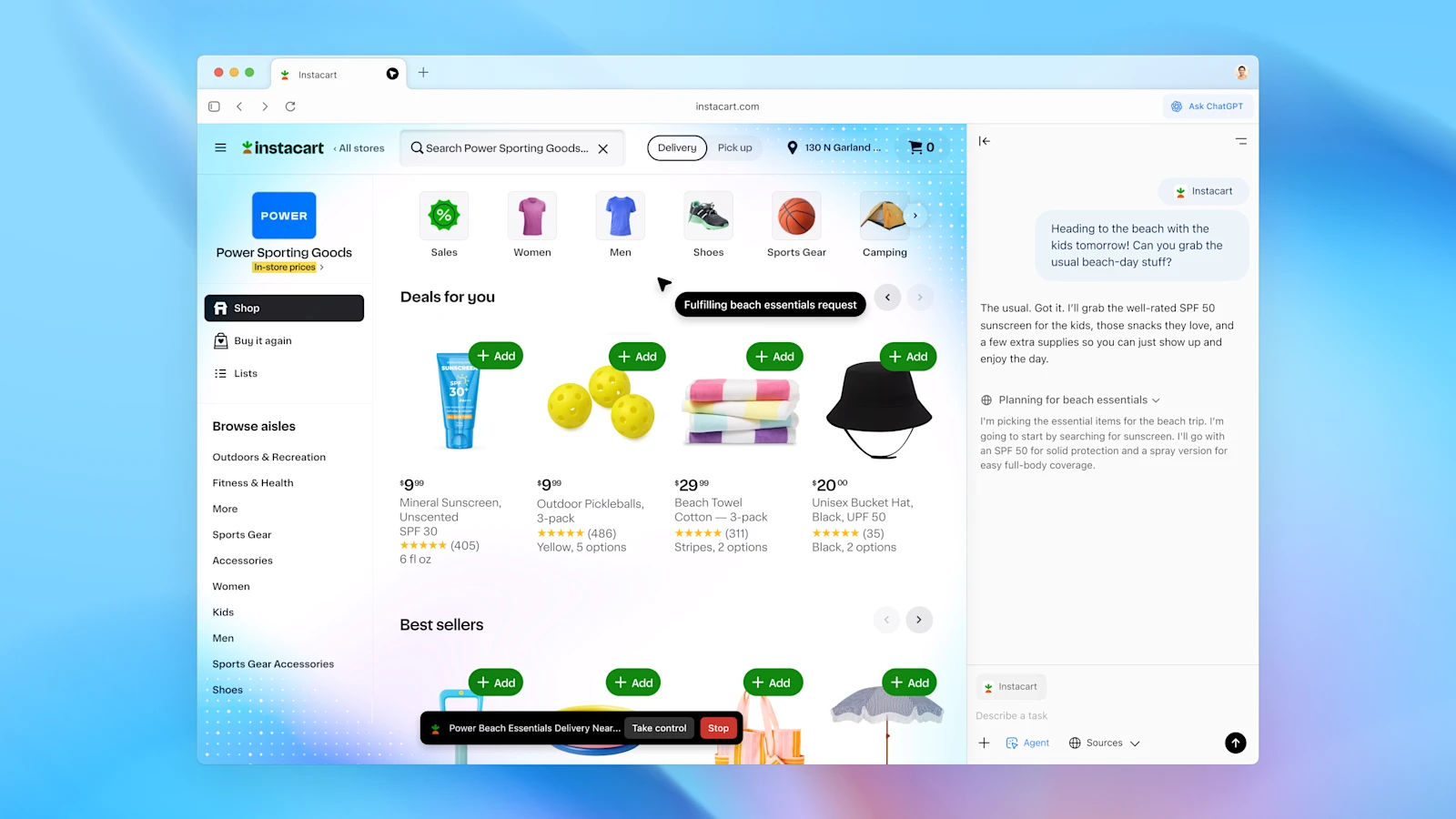
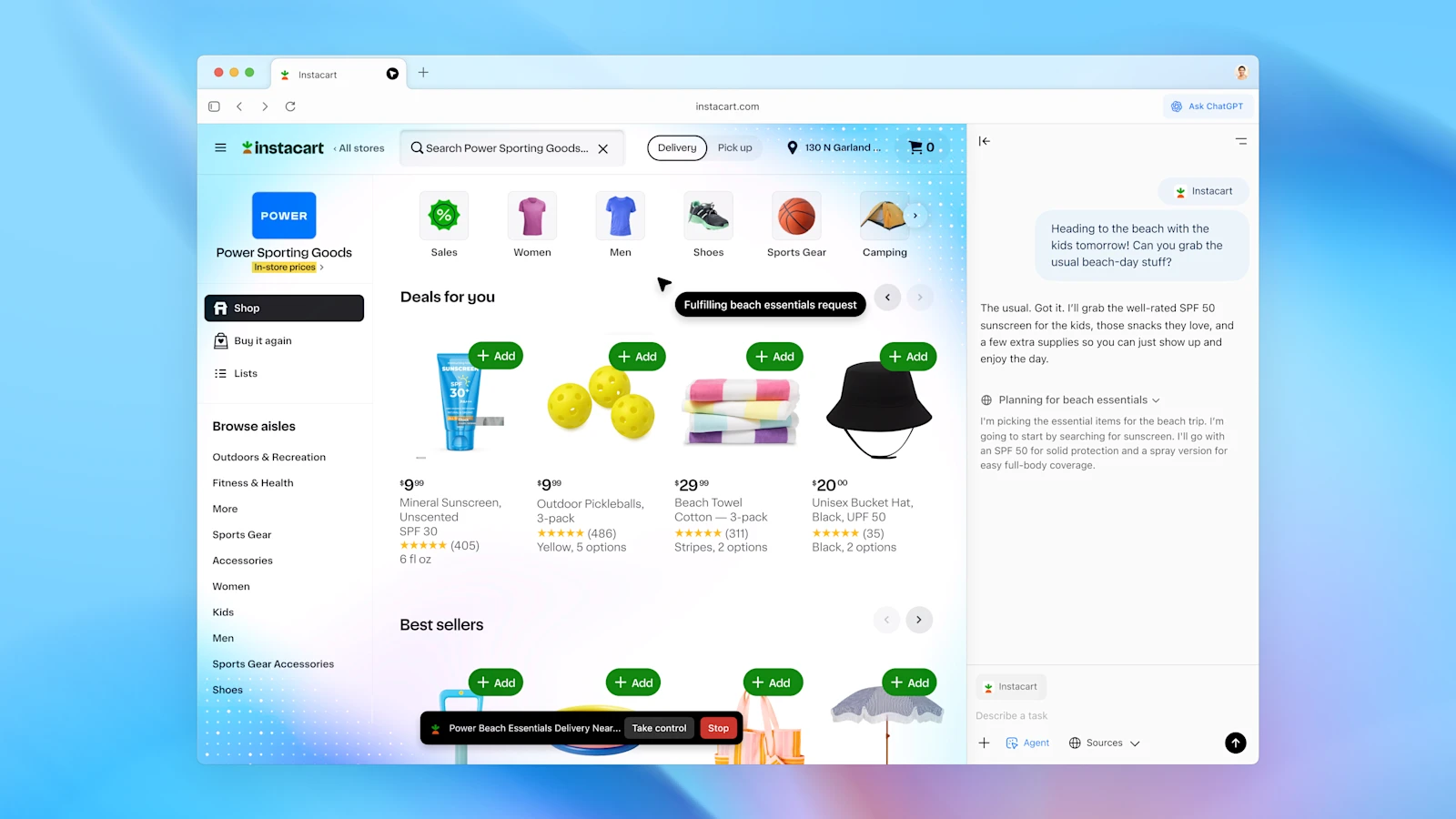
- A WIRED hands-on notes the Atlas “Ask ChatGPT” sidebar can be “moderately helpful at best” and sometimes confusingly wrong. Source: WIRED post.
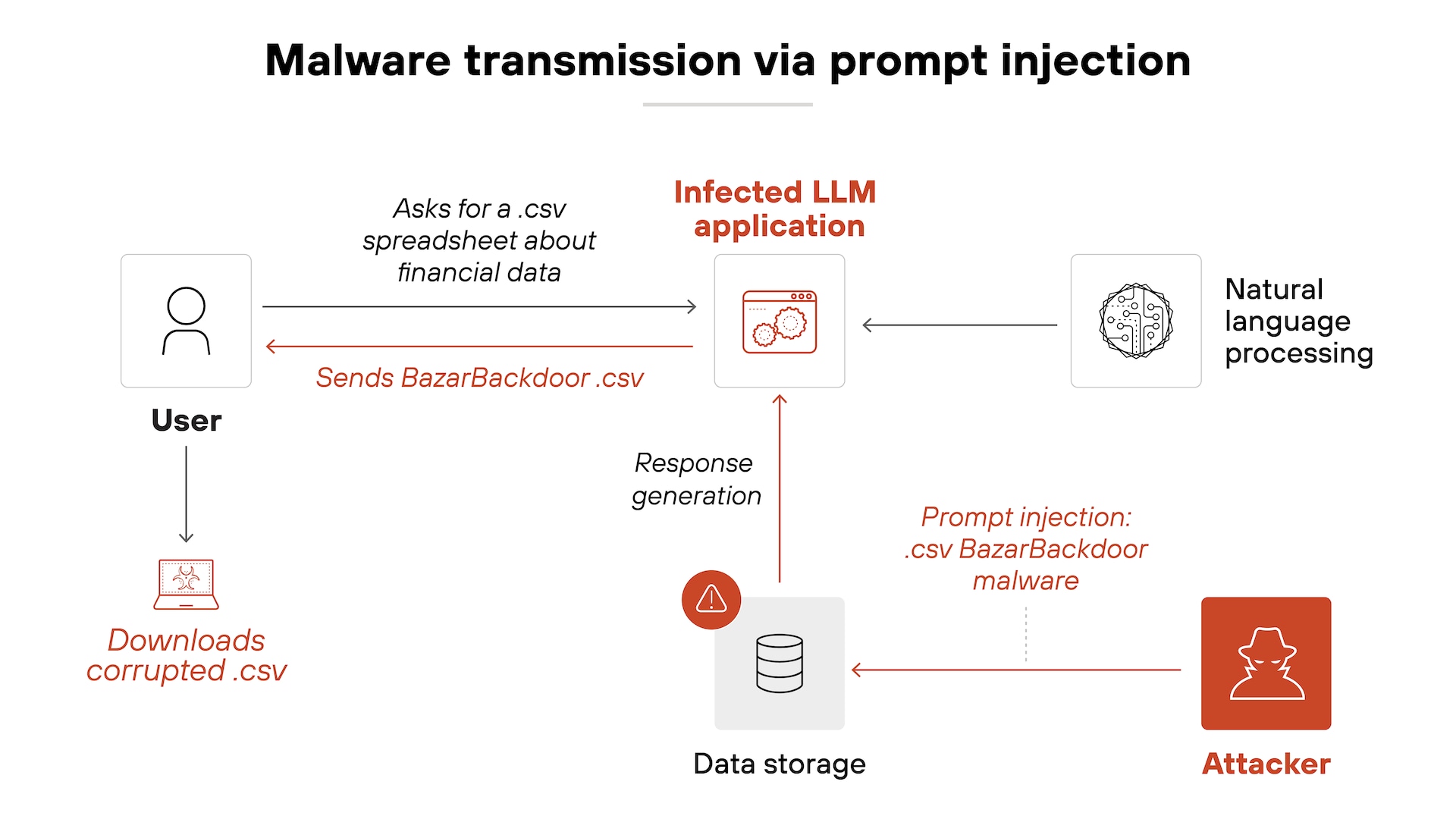
- TechRadar and others flag indirect prompt-injection concerns—malicious page content could steer the agent’s actions. Source: TechRadar.
- Even OpenAI security voices acknowledge prompt injection is an unsolved frontier. Source: simonwillison.net.
What this means for you / your team
Treat Atlas-style agents as early-stage tools. Keep tasks narrow, require human supervision, and validate outputs.
Security
- Limit the agent’s credentials and scope; avoid broad access by default.
- Assume pages can contain hidden instructions; sandbox actions where possible.
Reliability
- Do not rely on summaries or actions without verification.
- Use as a productivity aid, not a replacement for due diligence.
Bottom line
Agent-enabled browsing is compelling—and raw. Proceed with guarded optimism: clear task boundaries, least-privilege access, and consistent human oversight.

Comments
Post a Comment